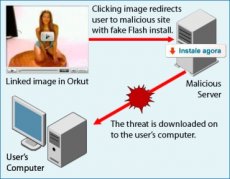
The soon-to-be-victim clicks the link and then he is prompted to install what it looks like a flash player upgrade (“flashx_player_9.8.0.exe”), from an external site. When installed, the file injects malicious Javascript code into their next active Orkut web session and the malicious scrapbook entry is sent to all his friends.
At present time, over 13,000 users have already been infected, and the numbers more than likely to go much higher if Google (the owner of Orkut) doesn’t step in with a quick fix.
Last December, another worm made it into the accounts of over 655,000 Orkut users before Google could take care of it.
An analysis on the W32.Scrapkut is available on Symantec’s site. According to it, you need not worry for the time being, as the malware seems to be interested only in spreading itself.



